Notification Channels
Notification Channels Overview
Notification Channels Overview
Notification Channels are destinations for Last9 to send notifications using webhooks or Integration APIs. We currently support Slack, Pagerduty, OpsGenie integrations. If you need any other channels to be supported, please get in touch via email or discord
Adding a Notification Channel
To add a notification Channel:
-
Navigate to Home → Notification Channels and click Add Channel
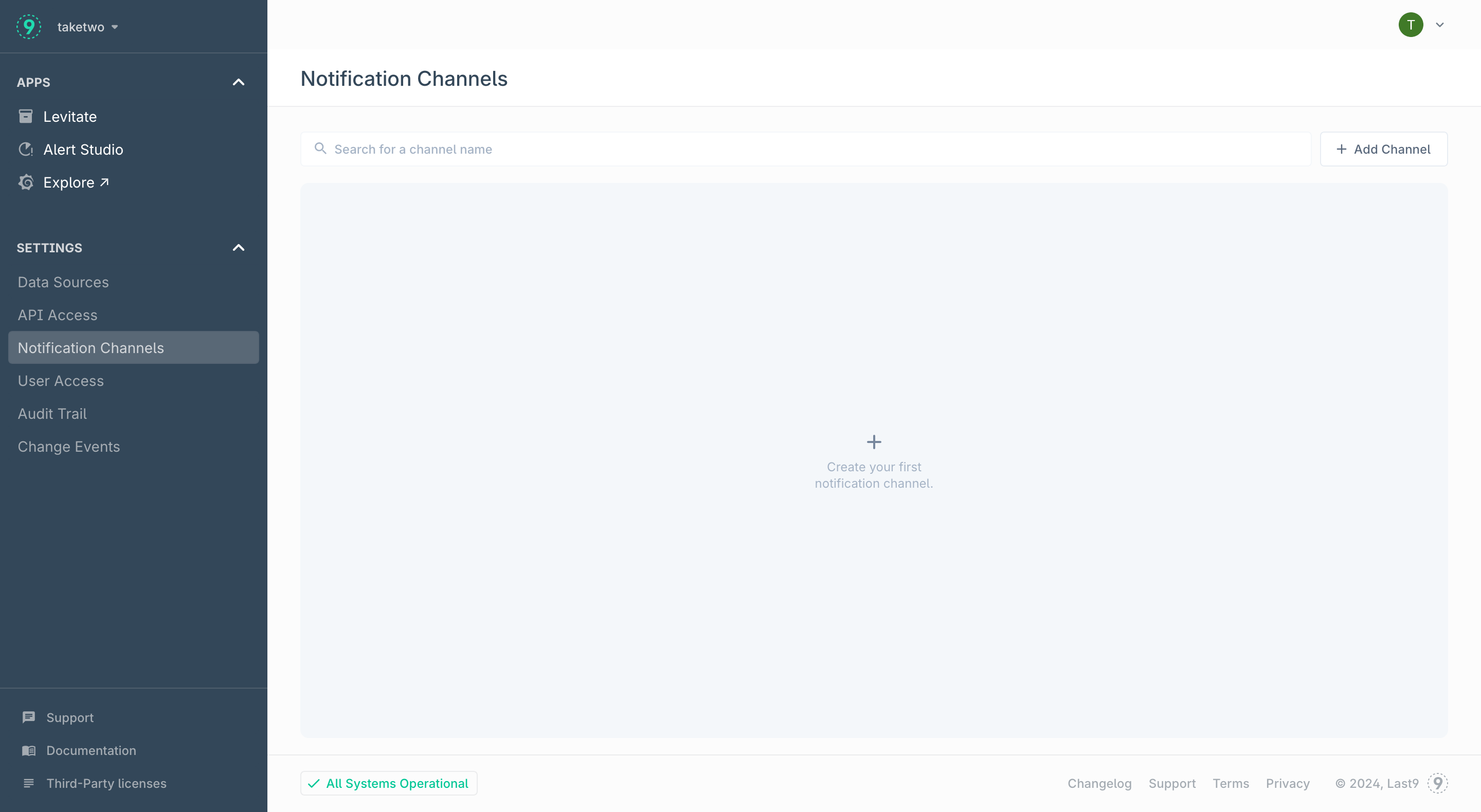
-
Provide the following details:
- Channel Name: Descriptive name that lets your team easily identify channel destination
- Channel: Choose a channel from the supported integrations list
- Webhook / Integration key: Refer to the linked integration documentation to retrieve the URL/API Key
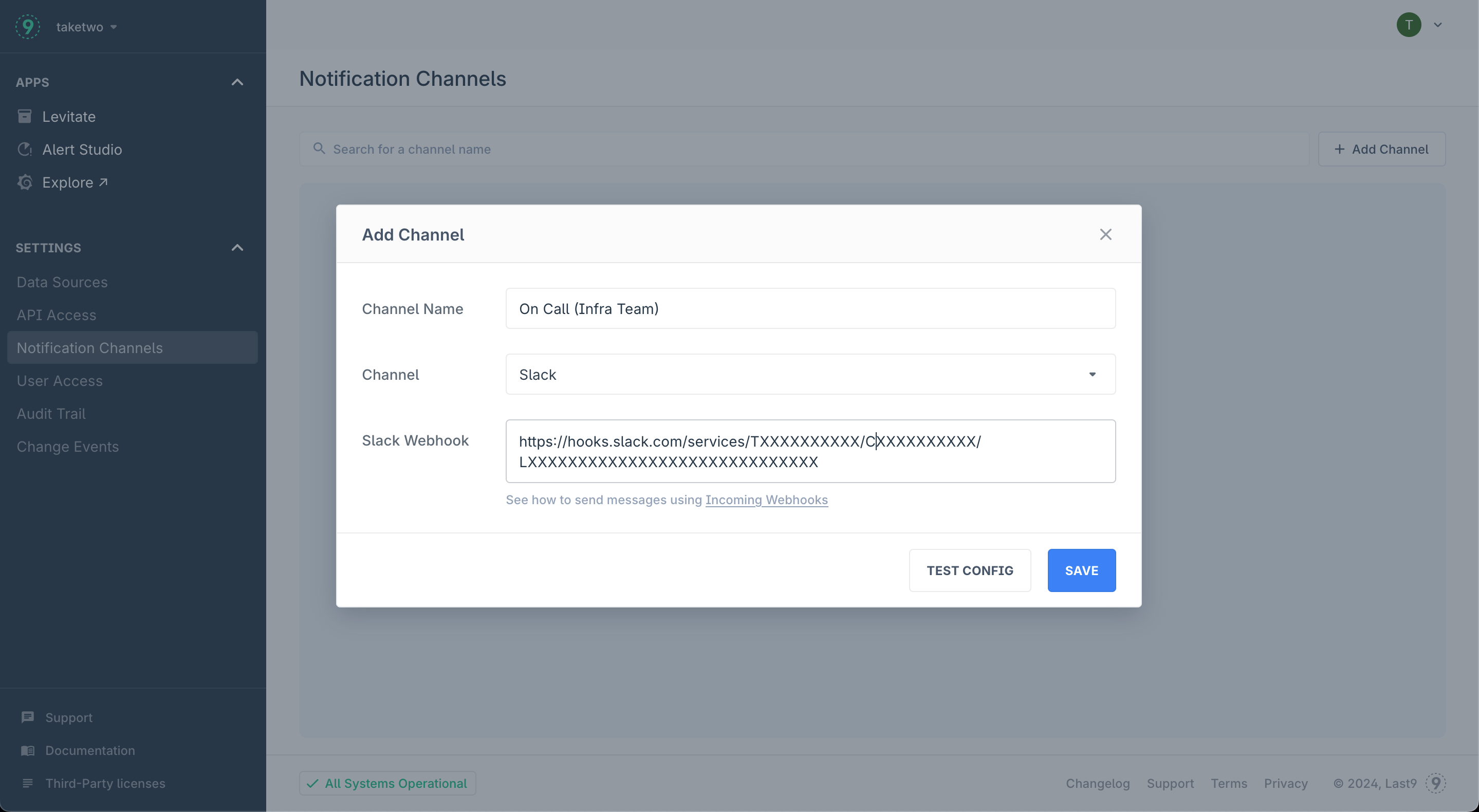
-
Press the Test config to check if you are able to receive the message in the configured channel
-
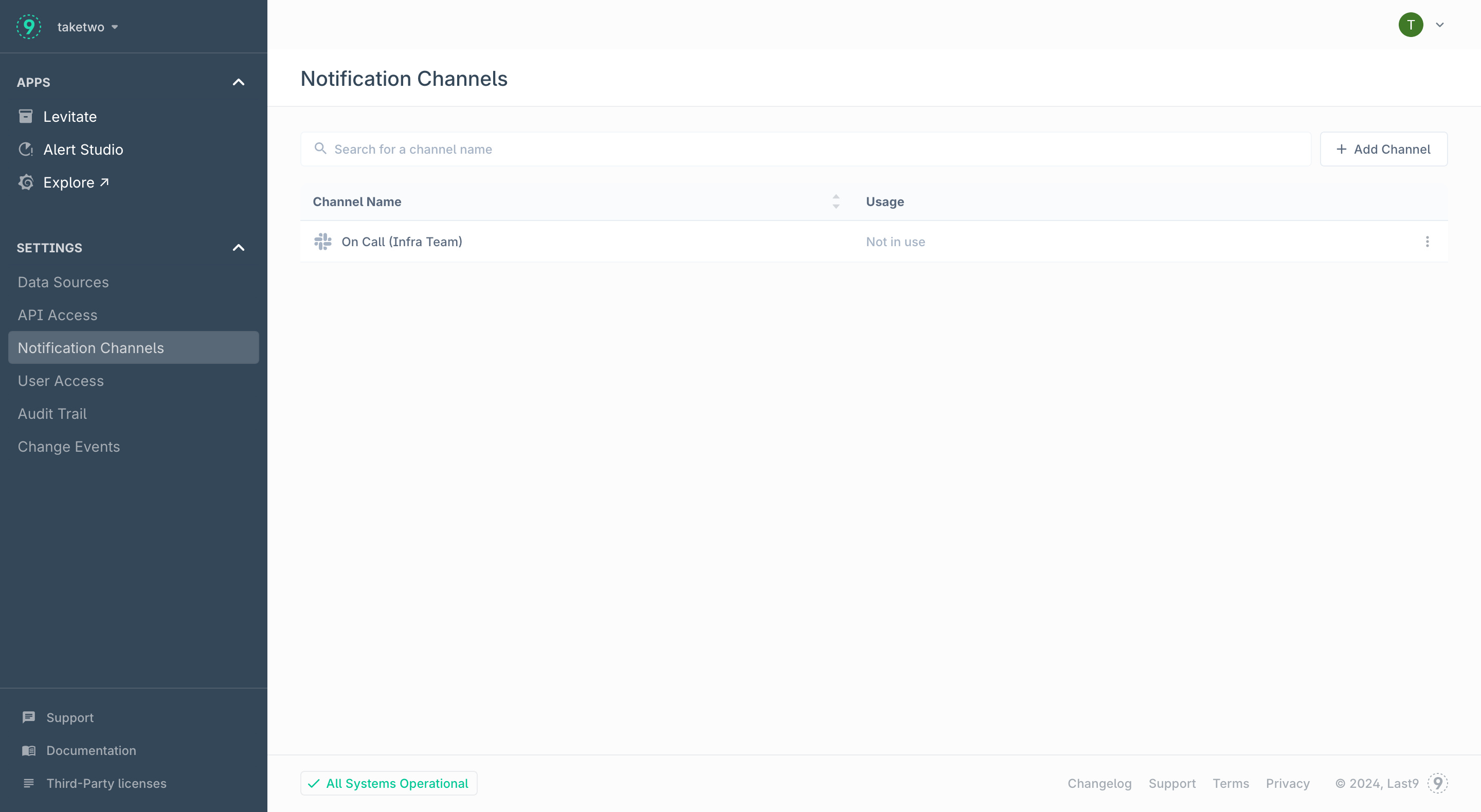
Press the Save button to enable this channel. This channel can now be used in Alert Groups to start receiving notification
Notification Payloads
Pagerduty
| Pagerduty field | Type | Description | |
|---|---|---|---|
| payload | object | ||
| payload.summary | string | Title for the incident | |
| payload.timestamp | timestamp | The ending time of this alert, in ISO 8601 format | |
| payload.severity | string | critical / warning for alerts marked as breach/threat in alert rule | |
| payload.source | string | Dedup key for the incident | |
| payload.component | string | Empty | |
| payload.group | string | Dedup key for the incident | |
| payload.class | string | Alert Rule Type | |
| payload.custom_details | object | Described below | |
| routing_key | string | Pagerduty integration key | |
| event_action | string | 'trigger' for active notifications, 'resolve' for resolved notifications | |
| dedup_key | string | Dedup key for the incident | |
| client | string | "Last9 Dashboard" | |
| client_url | string | Link to health dashboard for the alert in Last9 | |
| links | array of objects | Empty array | |
| images | array of objects | Empty array |
Custom Details
alert_condition- Condition set on alert. Static alerts, it is of the format.expr > 10based on the threshold configured. For pattern-based alerts, it is of the formatalgo_type(tunable, expr). For example, for a high spike alert set with tunable 3, this would behigh_spike(3, expr)algo_type- Type of alert (static_threshold,increasing_changepointetc)client_url- Link to the health dashboard for this alert on Last9description- Description of the alert. If a description is provided while configuring the rule, it appears here. Otherwise, a default description based on the algorithm, indicator, and entity is shownstart- Starting time of this alert, in ISO 8601 formatend- Ending time of this alert, in ISO 8601 formatexpression- Name of the indicatorentity_name- Entity nameentity_type- Entity typeentity_team- Entity team. IsNoneif not assignedentity_tier- Entity tier. IsNoneif not assignedentity_workspace- Entity workspace. IsNoneif not assignedentity_namespace- Entity namespace. IsNoneif not assignedseverity- Severity of the alert (breach/threat)notification_call- Whether this alert is sent for the first time or repeated (first/repeat)runbook- Link to the runbook for this alert (has to be configured while setting up alert). This key is omitted if the runbook isn’t configured- If the entity under alert has
tagsassociated with it, they are included in custom details astag_<tag_name>=true time_in_alert- Duration for which this alert was observed. E.g., 8 in 10 minutes.
OpsGenie
| Opsgenie field | Description | Type |
|---|---|---|
| message | Title for the incident | string |
| alias | Dedup key for the incident | string |
| description | Description of the alert. If a description is provided while configuring the rule, it appears here. Otherwise, this field is omitted. | string |
| tags | Tags associated with the entity | array of strings |
| actions | ["Debug"] | array of strings |
| details | Described below | object |
| entity | null | string |
| source | Last9 Dashboard | string |
| note | A string description of the alert, along with the health dashboard link for the alert | string |
| responders | Not used | array of objects |
| visibleTo | Not used | array of objects |
| priority | Not used | string |
| user | Not used | string |
Details
alert_condition: Condition set on alert. Static alerts, it is of the format.expr > 10based on the threshold configured. For anomaly alerts, it is of the formatalgo_name(tunable, expr). For example, for a high spike alert set with tunable 3, this would behigh_spike(3, expr)algorithm: Type of alert (static_threshold,increasing_changepointetc)component:nulllast9_dashboard: Link to the health dashboard for this alertexpression: Name of the indicatorservice: Name and type of the entitysource: Dedup key for this incidententity_name: Entity nameentity_type: Entity typeentity_team: Entity team. IsNoneif not assignedentity_tier: Entity tier. IsNoneif not assignedentity_workspace: Entity workspace. IsNoneif not assignedentity_namespace: Entity namespace. IsNoneif not assignedseverity: Severity of the alert (breach/threat)notification_call: Whether this alert is sent for the first time or repeated (first/repeat)runbook: Link to the runbook for this alert (has to be configured while setting up alert). This key is omitted if the runbook isn’t configured
Troubleshooting
Please get in touch with us on Discord or Email if you have any questions.