Alert Rules
Alert Rules Overview
Alert Rules Overview
Alert Rules evaluate Indicators using algorithms and configured thresholds/sensitivity to generate Alerts. Alerts can be visualized using Health and sent to configured Notification Channels.
Creating an Alert Rule
Before you can configure an Alert Rule, you need at least one Indicator to be created in the Alert Group.
To create an Alert Rule:
-
Navigate to the Alert Group in which you would like to create the Alert Rule: Home → Alert Studio → Alert Groups → Select an Alert Group → Alert Rules Tab
-
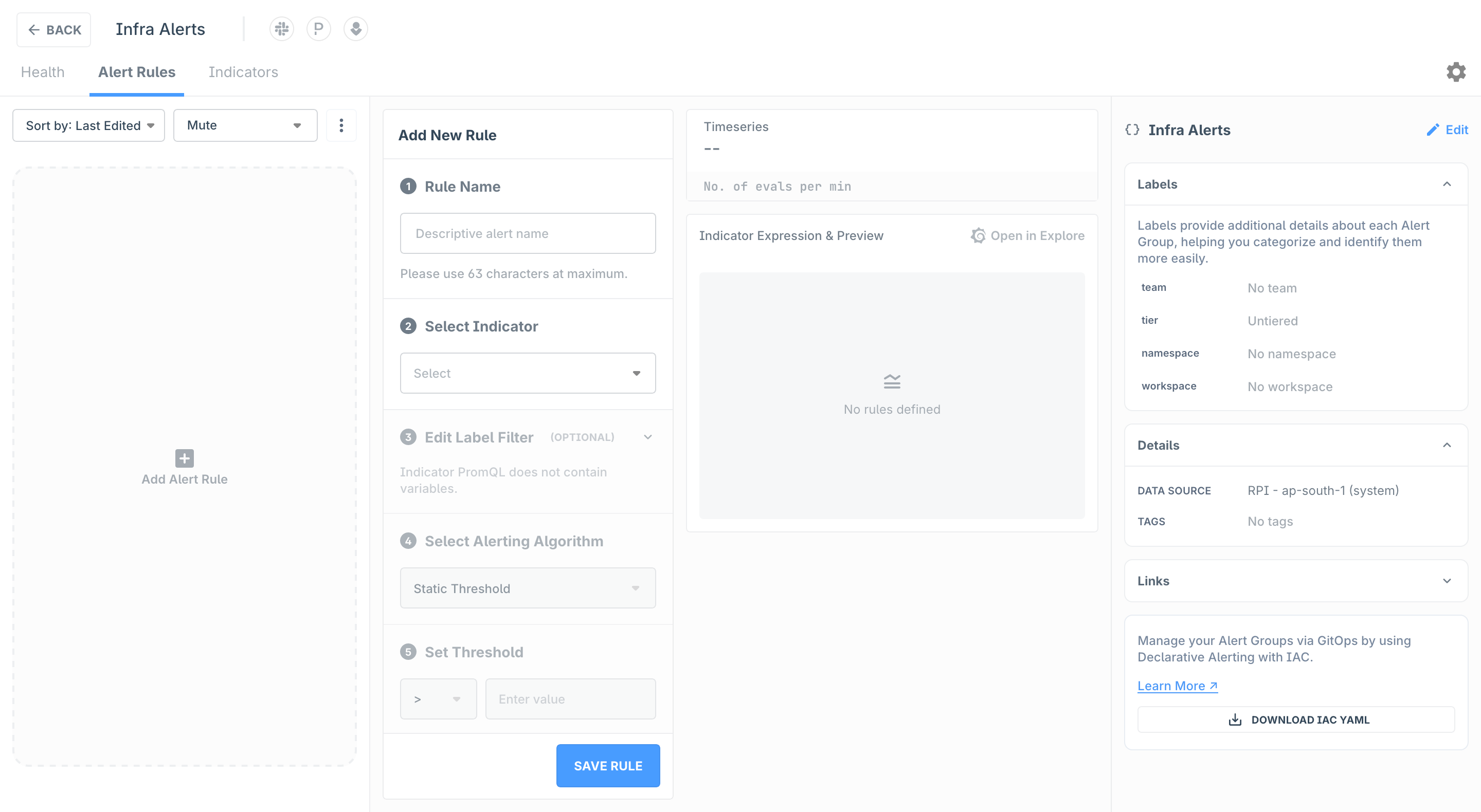
The following details are required for an Alert Rule:
-
Rule Name: Use a descriptive Alert Rule that can be easily identified by your team. This will be also sent as the part of notifications
-
Indicator: Select the indicator for which you would like to create the Alert Rule. If you have not created an Indicator, follow the steps as mentioned here
-
Edit Label Filter: ...
-
Algorithm: Select from the available algorithms. For a detailed guide on how various algorithms, refer to this guide In this tutorial, we will step up an alert using Static Threshold
-
Threshold / Sensitivity: Specify the Threshold (or Sensitivity in case of Anomaly Detection algorithms) and the Operator (example: Alert when the Indicator value is greater than or equal to 10)
-
Alert Sensitivity: Using Alert Sensitivity you can define how reactive is the Alert Rule. Alert Sensitivity requires two inputs:
- Total Minutes: This is the total duration of the rolling time window during which the Indicator is evaluated, with the maximum allowed duration being 60 minutes. (All Alert Rules are evaluated in one-minute intervals)
- Bad Minutes: This value represents the number of minutes within the evaluation window that exhibit undesirable or unexpected behavior. These “bad” minutes need not be consecutive
If the number of 'Bad Minutes' exceeds the predefined limit within the 'Total Minutes' rolling window, an alert is generated. A rolling time evaluation window offers continuous analysis by constantly updating the period under evaluation. It allows for immediate reaction to issues as they develop, rather than waiting for a static hourly evaluation to complete.
This mechanism ensures that users are notified only when there is a significant deviation in expected metric performance, helping to avoid unnecessary alerts for minor or inconsequential fluctuations.
-
Severity Level: Helps you provide additional context to Alert Rule by categorizing alerts as either Threat or Breach. We indicate Threat alerts in amber and Breach as red colors
-
Notification Group: For Indicators with multiple timeseries, you can choose to receive individual alerts for every single timeseries or to group them into a single alert. We recommend that you group alerts as ungrouping them can lead to noise being generated
-
Annotations (Optional): Annotations are optional information labels in
key:valueformat that can be sent with every Alert notification. You can use these specify additional description, Runbooks or trigger complex workflows in your incident management systems -
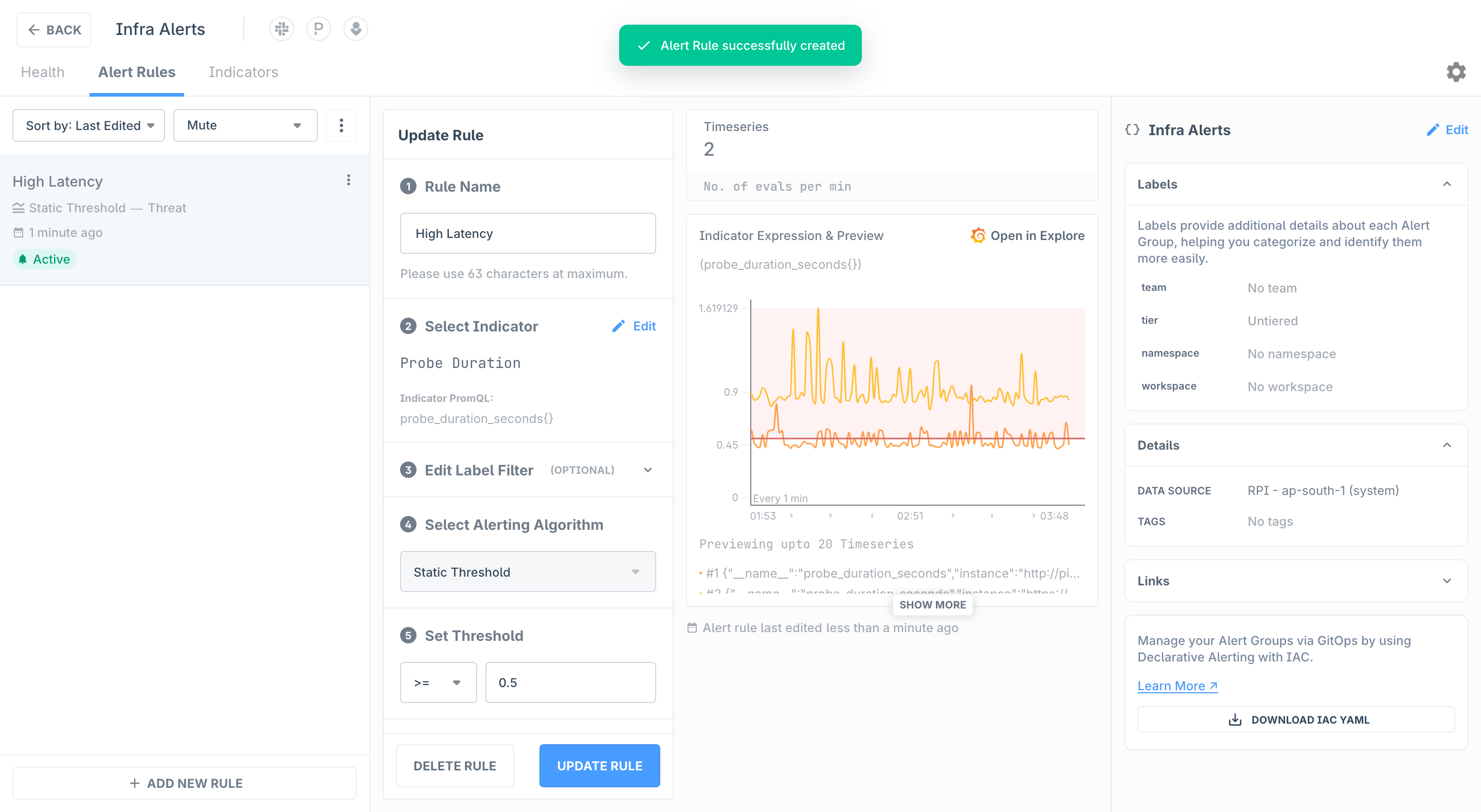
When the threshold is configured, we generate a preview to help you visualize what values of the Indicators are considered anomalous. The number of timeseries that will be evaluated every minute by the alert rule are indicated
Click Save Rule to enable alerting for this rule. To start receiving notification for this Alert Rule, ensure that at least one Notification Channel as been configured for this Alert Group.
-
Troubleshooting
Please get in touch with us on Discord or Email if you have any questions.