Send data using AWS PrivateLink
This guide walks you through how to configure AWS PrivateLink for use with Last9 will send read and write requests over the private network.
Overview
The process consists of configuring an internal endpoint in your VPC, which can talk to the Last9 endpoint without going via a public network.
Setup
Get Last9 PrivateLink Service name
Currently, Last9 supports three regions - eu-west-1, us-east-1 and
ap-south-1.
You can choose the service name from the following list.
This applies only to customers hosted on app.last9.io. If you use an on-premise hosted Last9 offering, the Last9 Customer Success team will provide the right endpoint details. Please contact us at cs@last9.io.
| Region | Type | Service Name | DNS |
|---|---|---|---|
eu-west-1 | Write | com.amazonaws.vpce.eu-west-1.vpce-svc-0381436dec59e8895 | https://app-tsdb-euw1.last9.io |
eu-west-1 | Read | com.amazonaws.vpce.eu-west-1.vpce-svc-0a101a671bd82e759 | https://read-app-tsdb-euw1.last9.io |
us-east-1 | Write | com.amazonaws.vpce.us-east-1.vpce-svc-0eda8f4ecd25af01f | https://app-tsdb-use1.last9.io |
us-east-1 | Read | com.amazonaws.vpce.us-east-1.vpce-svc-0fb0502d1f58dc1bb | https://read-app-tsdb-use1.last9.io |
ap-south-1 | Write | com.amazonaws.vpce.ap-south-1.vpce-svc-0240de6d26b096123 | https://app-tsdb.last9.io |
ap-south-1 | Read | com.amazonaws.vpce.ap-south-1.vpce-svc-01c9bdbb02e34fe2c | https://read-app-tsdb.last9.io |
us-east-1 | Read/Write | com.amazonaws.vpce.us-east-1.vpce-svc-06931cb6d013ad0fc | https://otlp.last9.io |
ap-south-1 | Read/Write | com.amazonaws.vpce.ap-south-1.vpce-svc-026c2a0d782b7ef32 | https://otlp-aps1.last9.io |
ap-southeast-1 | Read/Write | com.amazonaws.vpce.ap-southeast-1.vpce-svc-0f8965c5096ad1f65 | https://otlp-apse1.last9.io |
Create an endpoint in your VPC
Navigate to the VPC section and select Endpoints in the left sidebar.
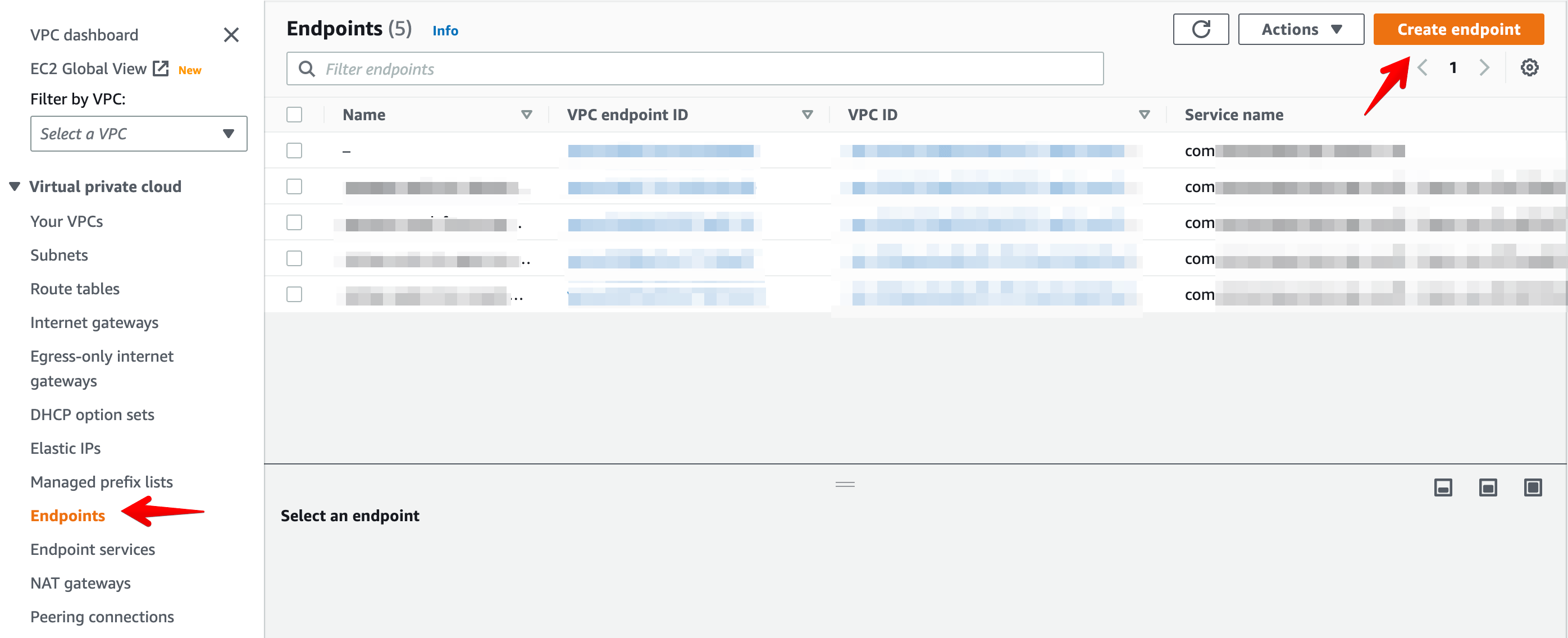
Click on Create Endpoint in the top right corner. Enter an appropriate
Name tag, and Select Other endpoint services .
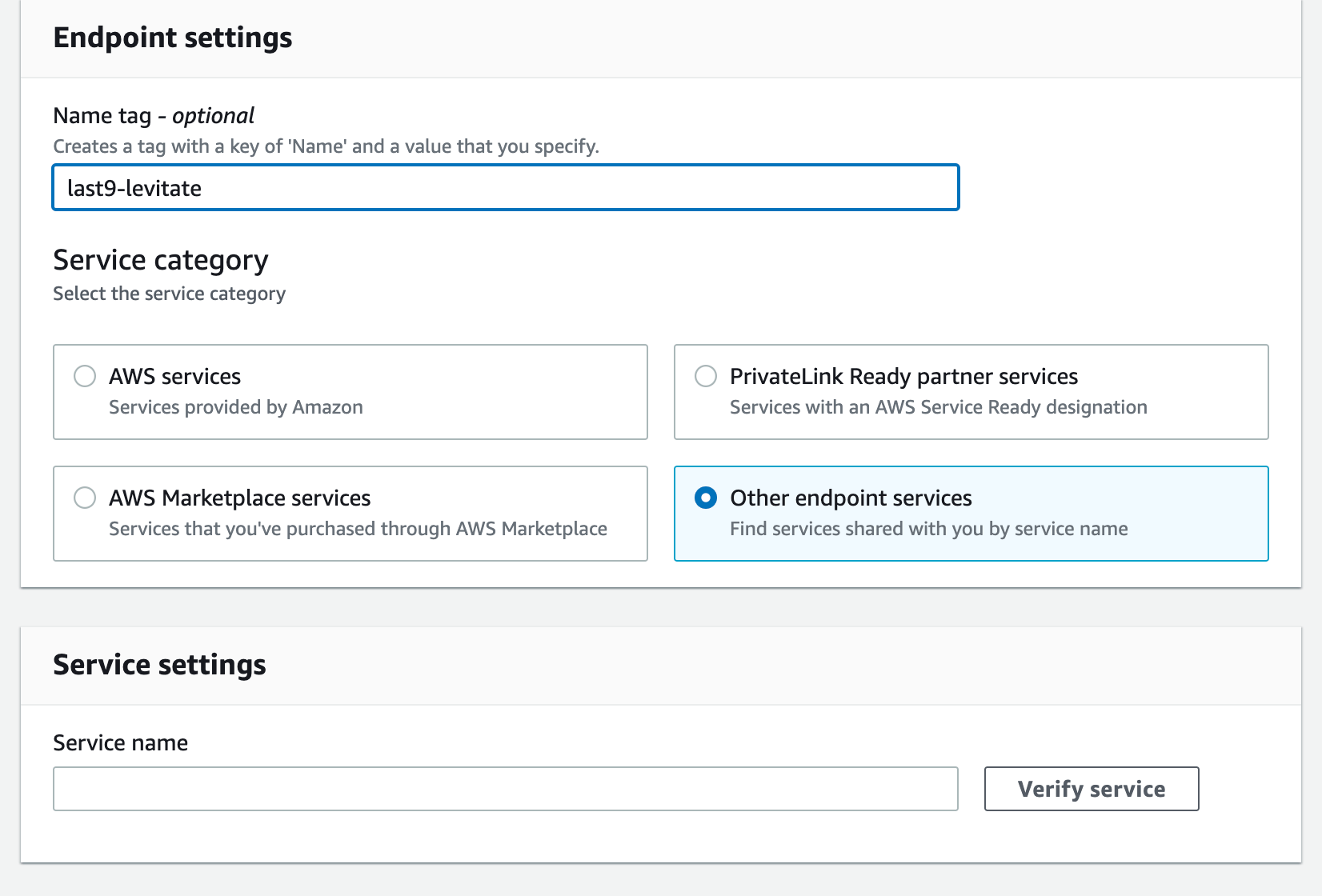
Enter the Service name provided by Last9 in the earlier step and Click
Verify service.
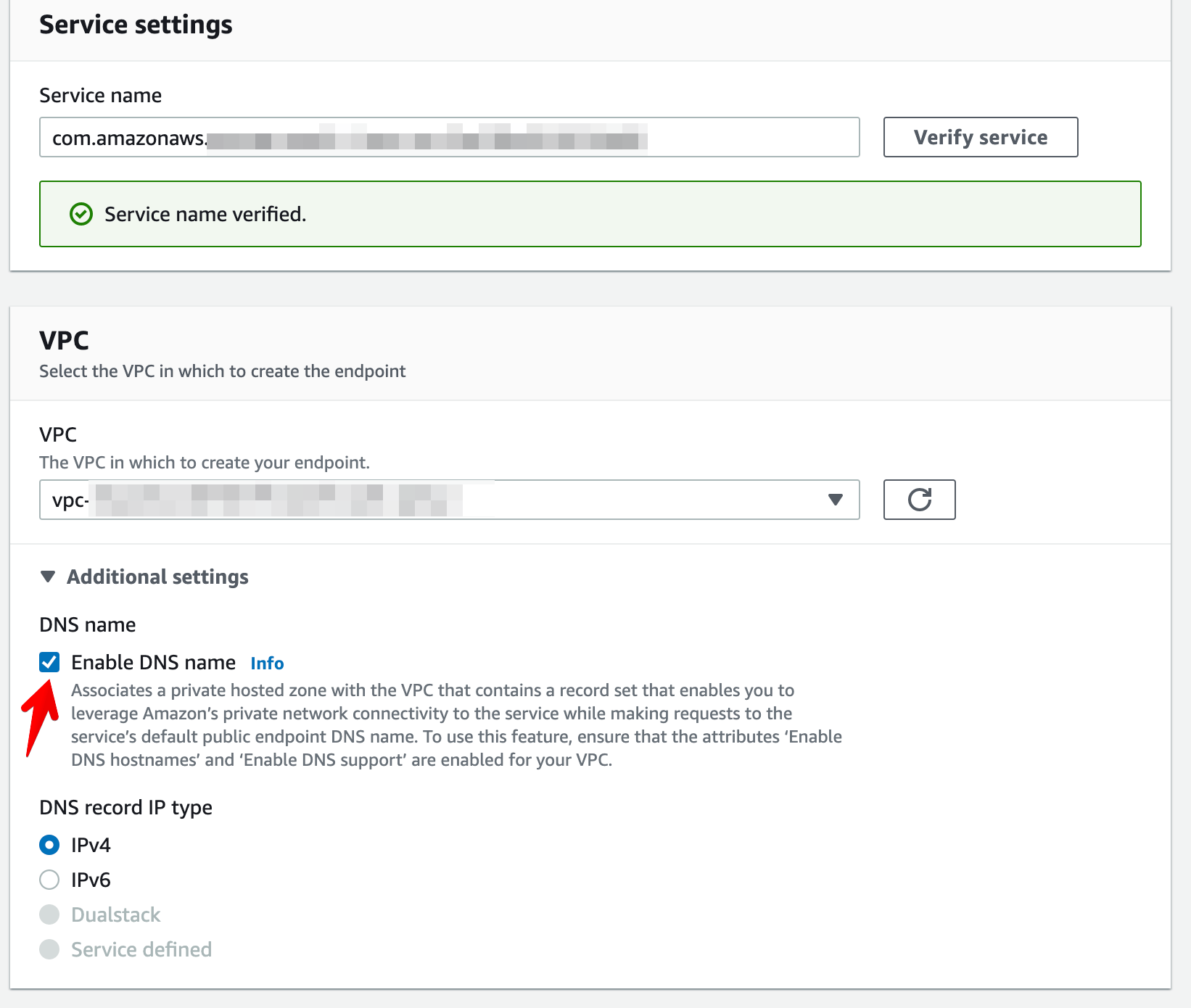
Additional settings
- Select the VPC for the endpoint, and in additional settings, check the box for
Enable DNS Name.
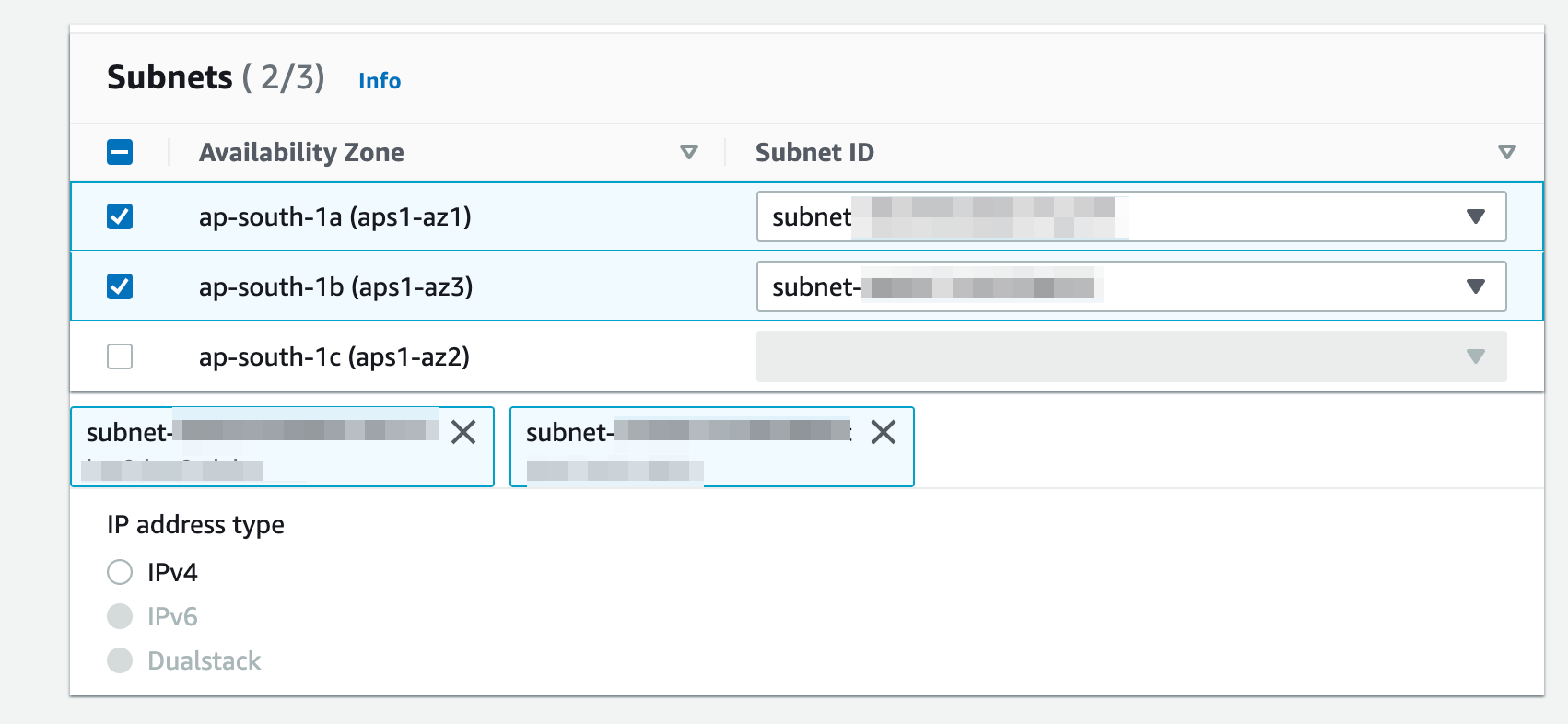
- Select the subnets where you are running the workloads that will read or write
to Last9.
- Attach a security group to the endpoint; the endpoint must allow traffic on port 443 from your origin VPC or the specific IP address where the requests originate.
- Note: For any on-premise Last9 setups, the endpoint must allow traffic for
ports 80 and 443.
Verification
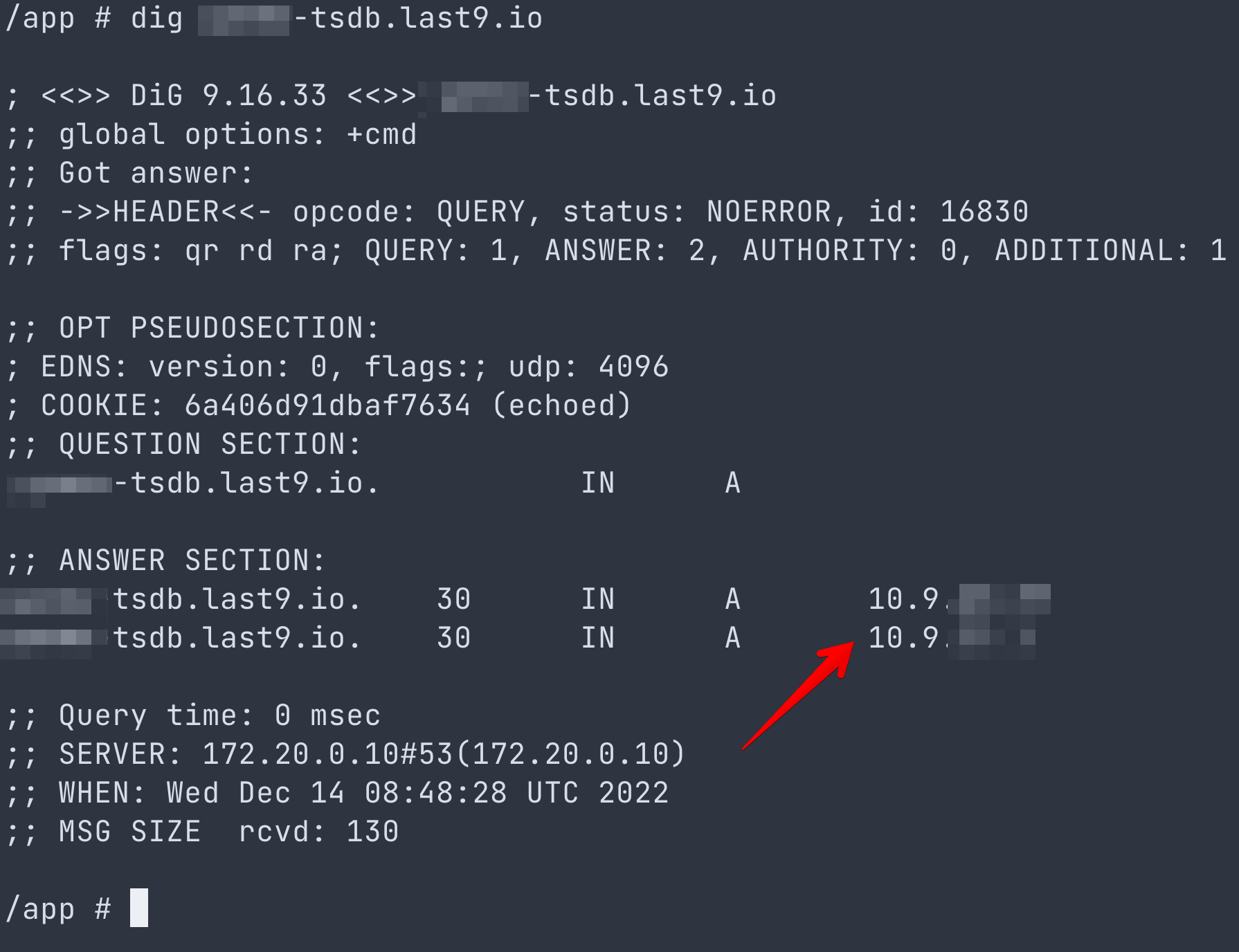
After the Endpoint status becomes available, validate that the DNS records change from any machine inside a subnet in your VPC for which the Endpoint is enabled.
For example, dig app-tsdb.last9.io should not return the public IP address;
instead, it should return the private IP address of the Endpoint we just
created.
That's all. Happy sending logs, metrics, and traces to Last9 using PrivateLink.
Troubleshooting
Please get in touch with us on Discord or Email if you have any questions.